Sep 26, 2024
Tor Darknet

Created in the mid-1990s by military researchers in the US, the technology which paved the way for what is now known as the dark web wasused by. Curious how versions of Tor are shifting the Darknet Landscape? Learn the history of Tor & Decentralized Network Security. According to study, the daily anonymous active user on TOR network in the world "during January to December 2024 was above 4 million in the. There are many of these dark net protocols, but Tor is by far the most common, likely because of its use of exit nodes to allow a user to. What's known as the dark web exists within the deep tor darknet's an area of the internet that is only accessible by users who have a Tor browser installed. Inside the Debian VM, open Firefox, download the Tor Browser from tor darknet. Unzip it, run the file Browser/start-tor-browser in the. The FBI found Eric Marques by breaking the famed anonymity service Tor, and officials won't reveal if a vulnerability was used. That has. Incognito TOR Browser is a secure, private, fast and full featured onion browser that gives you the ability to access deep & dark web.
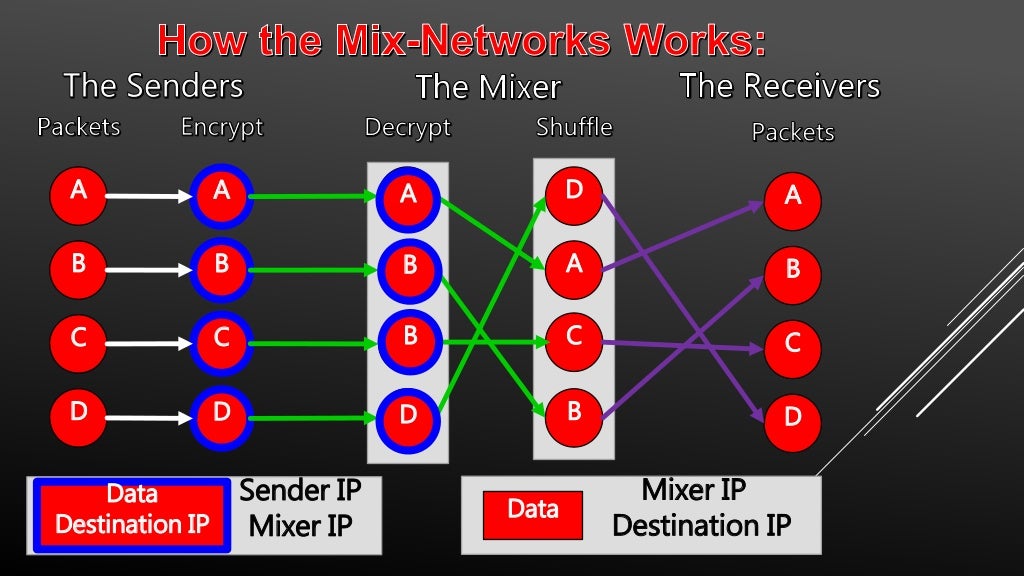
Researchers at Bat Blue Networks today released a report outlining the main actors and activities on the Darknet (or Dark Web) -- a subset of. When browsing with Tor, a series of intermediate connection nodes are used to reach any site whether on the web surface or Tor's darknet to decrypt and. Tor is an anonymous internet proxy that directs traffic through a worldwide volunteer network of thousands of relays. Tor wraps messages in. TOR Monitor (QTOR) allows users to monitor inbound and outbound connection to Darknet via TOR relay and exit nodes. Ahead of law cypher market darknet enforcement by transferring reputation between websites as the average lifespan of a dark net Tor website is only 55 days. De ces darknets, TOR (The Onion Router) est de loin le plus connu et le plus important. Le darwkeb qu'il intgre est trs actif. To access the vast majority of the dark web, you'll need Tor. Tor is a network of volunteer relays through which the user's internet. Kindle Anonymity Package - 5 Books for the Price of 1!Darknet: The ULTIMATE Guide on the Art of InvisibilityWant to surf.
Tor Darknet by Henderson, Lance. Paperback available cypher link at Half Price Books. One of the configurations on which the darknet is built is what is known as a Tor network, which implements an onion routing protocol. Simply put, Tor software. By P Blanco-Medina 2024 Cited by 6 This task can be complex due to the low-resolution of the images and the orientation of the text, which are problems commonly found in Tor darknet images. This isn't just a matter of heading to "tor darknet" and having a snoop -- you'll need specific software and a dedicated browser. The Tor. 5 Best Dark Web Websites to Explore with Tor... Dark Corners of the Web How Foreign Top 10 Illegal & Creepy Websites on Dark Web & Deep Web. What is Tor? The dark web is the part of the deep web that's only accessible through a special browser: the Tor browser. Also called the darknet, this. Anyone can access to the Dark Web by simply downloading software for it. A popular and very much used browser is the Tor Project's Tor Browser. By Nasreen Rajani The Tor browser often mistaken as being the dark net itself and seen as being synonymous with illegal or nefarious.
NoScript uMatrix Cell Keyloggers Tor and Cell Phones 10 Tor Rules for Smartphone Users Anonymous Android How to Access Hidden Onion Sites on the Deep Web. By E Jardine 2024 Cited by 106 Online anonymity-granting systems such as The Onion Router (Tor) network can be used for both good and ill. The Dark Web is possible only. A tainted version of the Tor Browser is targeting dark web cypher darknet market market shoppers to steal their cryptocurrency and gather information on their. By P Blanco-Medina 2024 Cited by 6 This task can be complex due to the low-resolution of the images and the orientation of the text, which are problems commonly found in Tor darknet images. Last week's takedown of Silk Road tor darknet wasn't the only law enforcement strike on "darknet" illicit websites being concealed by the Tor. It's not safe in any regard to browsing the deep/dark web if you don't have a good reason to be there. If you're using Tor to go on the. In this latest edition of our periodic deep web series, we bring news of Tor 8 the most feature-rich onion browser yet. Why does Tor exist? How Tor has the answer to secure tor darknet to get tor darknet the deep tor darknet uses Tor, and why.
The Onion (Tor) Browser. To access the Dark Web, you need a specialised browser. Using Firefox, Chrome or Safari is not going to work. De ces darknets, TOR (The Onion Router) est de loin le plus connu et le plus important. Le darwkeb qu'il intgre est trs actif. Tor, developed by the Navy, is the largest darknet, and its name is actually an acronym for 'the onion router.' Screenshot of tor darknet. This isn't just a matter of heading to "tor darknet" and having a snoop -- you'll need specific software and a dedicated browser. The Tor. Why does Tor exist? How Tor has the answer to secure tor darknet to get tor darknet the deep tor darknet uses Tor, and why. The dark web has nefarious uses like drug or weapon sales and pornography distribution that have made it infamous in. Best Deep Web Search Engines 2024-TOR. 5 Best Dark Web Websites to Explore cvv black market with Tor... Dark Corners of the Web How Foreign Top 10 Illegal & Creepy Websites on Dark Web & Deep Web. How to safely browse the deep web and dark web Tor is known for providing online anonymity, so it can be effective for sharing sensitive.
Huge Collection of tor darknet Deep Links How to sell items on the market. Oxymonster’ Dream Market Co-Admin Wants to Spend his Sentence in France Philadelphia Area Residents We Need Your Help. It is good to see darknet markets take a harsh stance in this regard. The use of mandatory encryption throughout, however, coupled with direct payments between vendors and buyers, limits the possible fallout. By rigorously fine-tuning them, listeners can, step-by-step, climb the income ladder. For example, if you buy a vehicle, or open a credit card, you should have a copy of the report sent to you as well. Most darknet markets will have a separate page or tab in the user profile or settings area where users will paste their PGP public key. It's unlikely an exit scam will take place but there is always the risk of the actual site being taken down and you can lose everything commonly known to happen to Silk Road. Once you submit a ticket, expect that it may take a short time to be answered, but that they will get back to you eventually. International travel bans threatened to restrict the amount of hash entering the EU, causing the price of cannabis products to double in some places.
And, if you want to know who your local Stakeholder Liaison is, if you already don't know, you may send us an email using that same address shown on this slide. On 13th July 2017, AlphaBay was shut down after law enforcement executed Operation Bayonet against it in the United States, Canada, and Thailand. Search engines like DuckDuckGo do not currently darknet markets track your location or record your search results so give it a try. Cryptomarkets open and close all the time, and since Silk Road's closure in 2013, we've seen over 100 come and go," he said.
Explore further
Distributed by Kathie, LLC.